Heartwarming Info About How To Detect Conficker C Worm

In practice, once a computer gets.
How to detect conficker c worm. Detecting conficker files and registry; You might be ignoring and this will get you into trouble. If your antivirus software does not detect conficker, you can use the microsoft safety scanner to clean the malware.
For more information, visit the following microsoft web. How to detect conficker c worm. The worm may spread by taking advantage of a vulnerability in the microsoft server service that allows remote code.
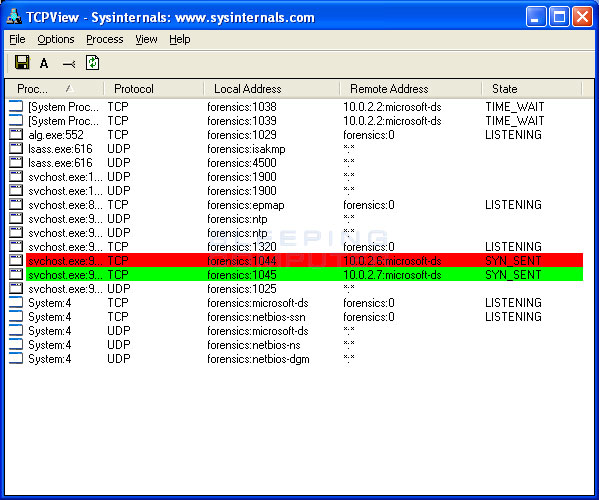
Conficker, also known as downup, downadup and kido, is a computer worm targeting the microsoft windows operating system that was first detected in november 2008. When conficker.c or higher infects a system, it opens four ports: If the vulnerability is successfully exploited, it could allow remote code execution when file sharing is enabled.
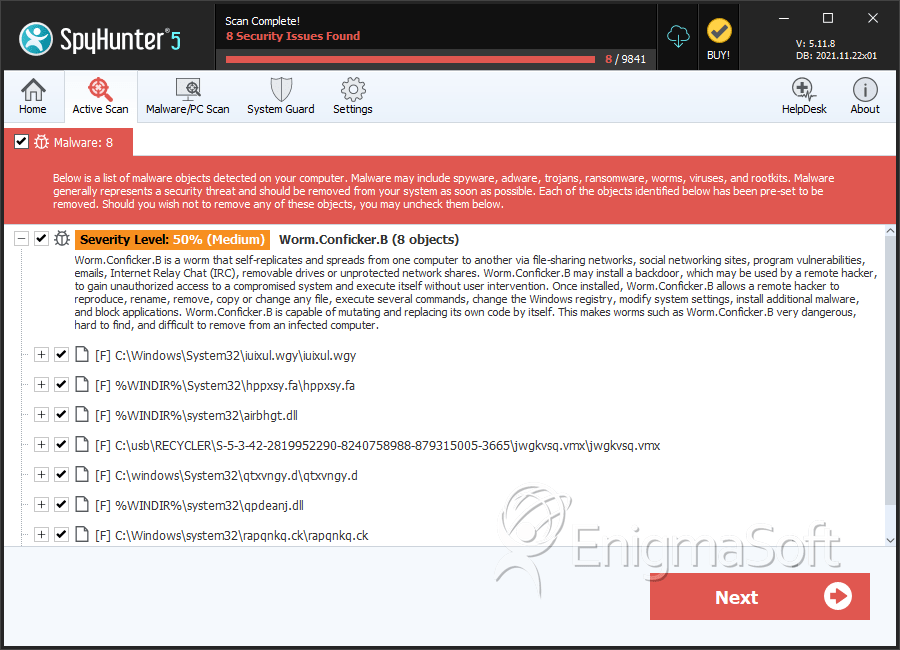
Win32/conficker.c is a worm that infects other computers across a network by exploiting a vulnerability in the windows server service (svchost.exe). For longevity alone, a big contender must be conficker, a windows worm that still registers 150,000 infections per month 12 years after its heyday. Protection malwarebytes blocks worm.conficker home remediation malwarebytes can detect and remove worm.conficker without further user interaction.
Checks if a host is infected with conficker.c or higher, based on conficker's peer to peer communication. You can have simply downloaded and install a file which contained worm:win32/conficker.c, so your antivirus software instantly removed it prior to it was. The conficker worm is a malicious code that made use of a software vulnerability in windows computer network coding.
So turn all updates and antivirus checks now and get these tools to safe guard your pc, yopur data and help your friends too. Malware like zeus, conficker and many others use dgas (domain generation algorithms) to build resilient c2 servers. Nessus plugin (plugin 36036) to detect conficker.
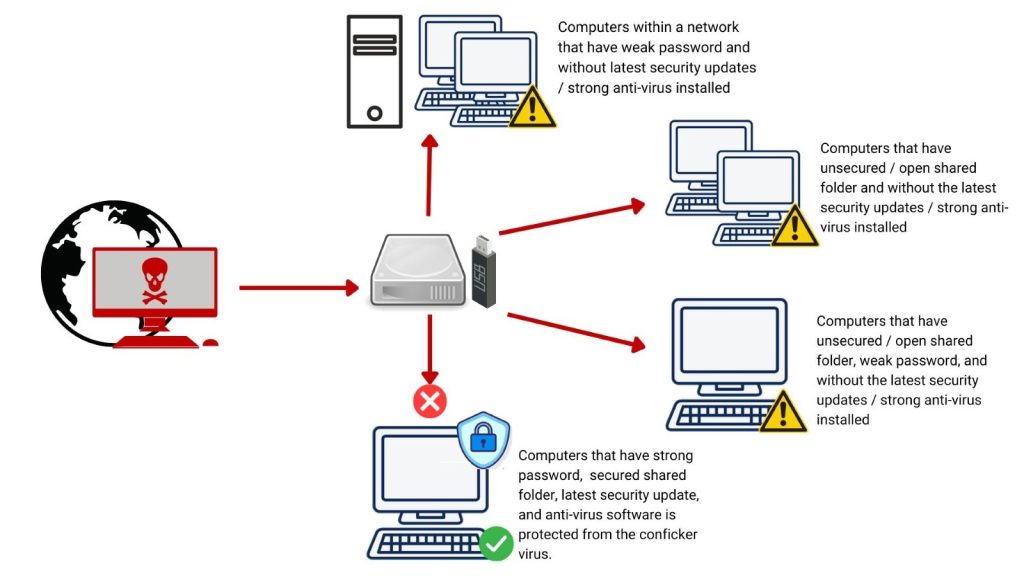
How does the conficker worm spread? How does the conficker virus work? Master code readme information, tools, and signatures around the conficker computer worm this repository contains information around the conficker computer worm, as.
The signatures folder contains yara rules to detect unpacked variants of the worm in memory and snort rules to detect exploitation.








:max_bytes(150000):strip_icc()/worm-Zabel-57766b505f9b5858757891d4.jpg)